Access Management in Amazon Redshift
August 2023 | 7-minute read

Tagged: AmazonRedshift | DataWarehouse | AccessManagement | AWSBestPractices | DataSecurity | DataAnalysis | IAMRoles | AWSGlue | AWSLambda | CloudSecurity | DatabaseManagement | Encryption | PermissionAssignment | DataIntegration | AWSArchitecture
Introduction:
Amazon Redshift is a fully managed data warehouse service provided by AWS. It is widely used for warehousing purposes and storing and analyzing very large amounts of data for business intelligence. It is known for its performance, scalability and security which makes it a suitable choice for enterprises of all volumes. Access Management in AWS Redshift can be understood as the process of monitoring and controlling who can access and perform actions on Redshift resources (clusters, schemas, individual tables or even individual columns/ rows). These accesses are traditionally managed by using concepts of IAM Users and Roles, Redshift Security Groups, Network Access, Database User Management, Encryption, etc.
Best practices:
The key features and capabilities of Redshift should also be thoroughly reviewed, including IAM users and roles, security groups, network access, database user management, and encryption.
IAM users and roles can be granted permissions to access Redshift resources, so it is important to assign least privilege to IAM users and to use IAM roles instead of shared access keys for applications that access Redshift. Additionally, enabling multi-factor authentication (MFA) for privileged IAM users adds an extra layer of security to protect against unauthorized access.
Another best practice is to properly configure security groups to control network access to Redshift clusters. Security groups act as firewalls for network traffic, and by properly configuring these groups, organizations can control access to their Redshift resources and protect their data. Network access can also be controlled using Amazon Virtual Private Cloud (VPC) to further secure the data.
Redshift also supports database user management, allowing organizations to create, modify, and delete database users, as well as grant and revoke permissions on Redshift databases and schemas. Proper database user management helps ensure that only authorized users have access to sensitive data, while reducing the risk of unauthorized access.
Finally, organizations should also use encryption to protect their sensitive data. Redshift supports encryption of data in transit and at rest, using SSL/TLS and Amazon Key Management Service (KMS), respectively. This helps ensure that sensitive data is protected both when it is being transmitted and when it is stored.
By following these best practices, organizations can ensure that their Redshift environment is secure, efficient, and reliable, and that their sensitive data is protected from unauthorized access and misuse.
Challenges:
- Managing a large number of users and permissions across multiple Redshift clusters and databases.
- Maintaining security and compliance of sensitive data stored in our Redshift clusters.
- Integration of Redshift with existing IAM systems
- Keeping track of changes to permissions and user accounts over a large period of time.
- Balancing ease of access for users with need for security and governance.
- Managing access centrally: Strenuous because Redshift is a shared resource, managing access across users and groups is a challenge especially when different users have access to different subsets of data.
- Managing security: Sensitive data security is one the biggest concerns of a shared resource like Redshift. It can be managed through authentication and authorization.
Solution overview:
In order to streamline a tedious process and alleviate the burden on administrative staff, a decision was made to implement a technical architecture utilizing Amazon Web Services (AWS). The proposed solution involves the creation of an MS Excel file containing relevant user information, which is then uploaded to an Amazon Simple Storage Service (S3) bucket for storage.
The Excel file will contain crucial details such as usernames, group names, and other information that is necessary for the proper assignment of permissions.
Technical Architecture:
To ensure efficient and secure permission assignment, a combination of AWS Glue and AWS Lambda is utilized. AWS Glue is a fully managed extract, transform, and load (ETL) service that makes it easy for customers to prepare and load their data for analytics. This service is particularly useful for the crawlers, which trigger an AWS Lambda function once the Excel file is uploaded. The Lambda function, written in Python, reads and converts the file into the necessary format, subsequently assigning the appropriate permissions.
Since this file contains critical information, the security of the data is of the utmost importance. To that end, built-in security features provided by AWS, such as server-side encryption on Amazon S3 and encryption in transit using AWS Key Management Service (KMS) on AWS Glue, have been integrated to ensure data encryption both at rest and in transit. This ensures that the data is protected from unauthorized access and breaches.
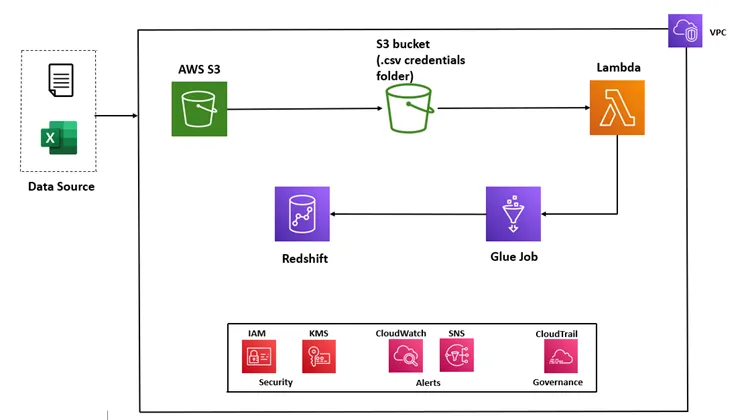
Architecture — Redshift Access Management
To ensure smooth operation and swift resolution of rare failure cases, a number of services have been employed. AWS CloudWatch is used to collect and track metrics, monitor log files, and set alarms, while AWS CloudTrail is used to log and track account activity. These services allow for the monitoring of the system, providing insights into how the system is performing, and identifying potential issues that may arise.
In addition, Amazon Simple Notification Service (SNS) is used to send messages between distributed systems, microservices, and applications. SNS allows for the sending of notifications to a variety of endpoints, such as email addresses and mobile phone numbers. This enables the system to send alerts and notifications in the event of any issues, allowing for swift resolution and minimizing downtime.
Overall, the proposed technical architecture aims to streamline the process of permission assignment, reducing the workload on administrative staff, while ensuring the security and integrity of the data. The use of AWS services such as S3, Glue, Lambda, CloudWatch, CloudTrail, and SNS provide a robust and reliable solution that can be easily integrated into existing systems.
Conclusion:
Centralized access management on Amazon redshift is crucial because it provides a single point of control for managing access to the database. This helps ensure consistent and accurate enforcement of security policies and reduces the risk of human error. It also simplifies auditing and compliance reporting, as all access activity can be tracked and monitored from a single location. Additionally, it is easier to manage access for large numbers of users, as changes can be made in one place and automatically propagated to all relevant users. This helps improve efficiency, reduce administrative overhead, and maintain a high level of security for the data stored in the database. By implementing the solution for access management mentioned above, the process of access management is expected to be streamlined and accelerated. Having the template for this idea could be useful as most of the projects we focus on as a company are data warehousing related.
To learn more about Ganit and its solutions, reach out at info@ganitinc.com.



